There are 3 high level elements in responding to a data breach or hack of an Oracle database; within these high level areas there are many smaller steps and hoops to jump through so I am not going to list everything here but will cover the basic parts. The three steps are:
- Manage the breach: Properly assess if a breach was reported and most likely occurred and then manage it via a dedicated process and ideally team.
- Perform live response: this means gathering the transient data evidence from the database and other relevant systems before it is lost due to time or other movements of the data. Then also gather the less transient evidence from the database and other relevant systems.
- Perform forensic analysis: This is to try and establish the why, how, when and who of the attack in a time line and the data checksummed to prove the validity of the data as it was extracted from the database.
PFCLForensics version 2024 is our product / tool that can be used to help manage and complete a breach response. I am going to show a brief overview here of some of the main features and functions of the tool and we are not looking at a specific attack but showing the features of the tool and how they operate.
On opening the software create a new project and you are given a check list to tick off my one person as the breach response progresses:
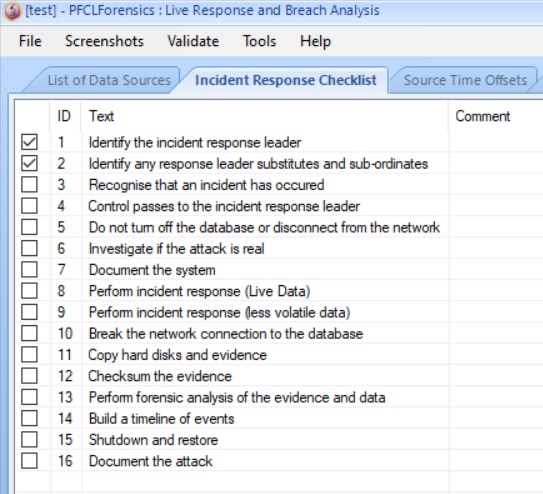
This allows management of the whole process; the list can be saved to the project and the list can be edited and changed as desired as the work progresses.
The next step is to connect PFCLForensics to the database to do the live response and gather the transient. The user needed to connect should have CREATE SESSION and SELECT ANY DICTIONARY. If a breach has occurred then it makes sense to not change the database to add users or grant privileges so either use an existing suitable user.
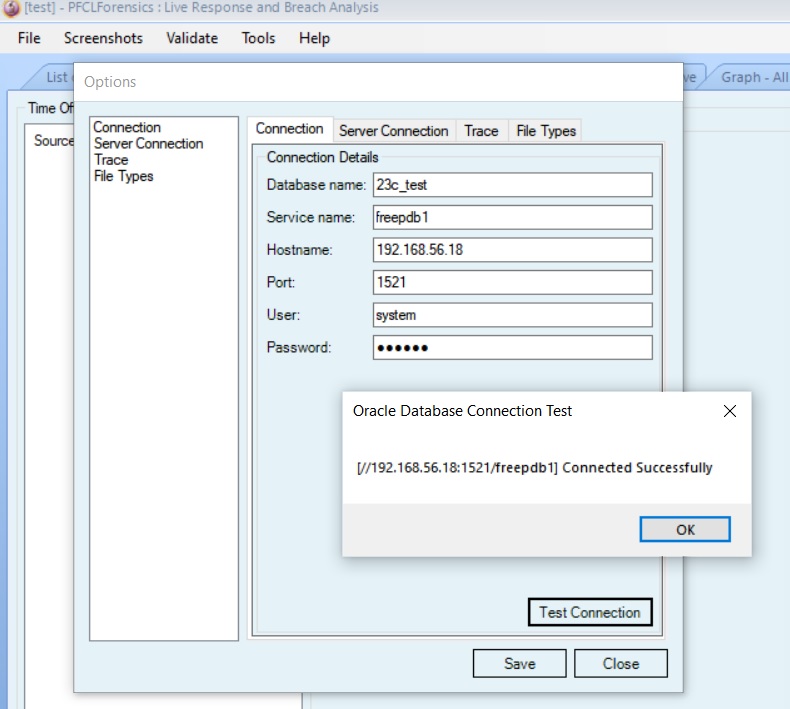
After we connect, choose the menu options to collect the transient data for an Oracle database and then the static data for an Oracle database:
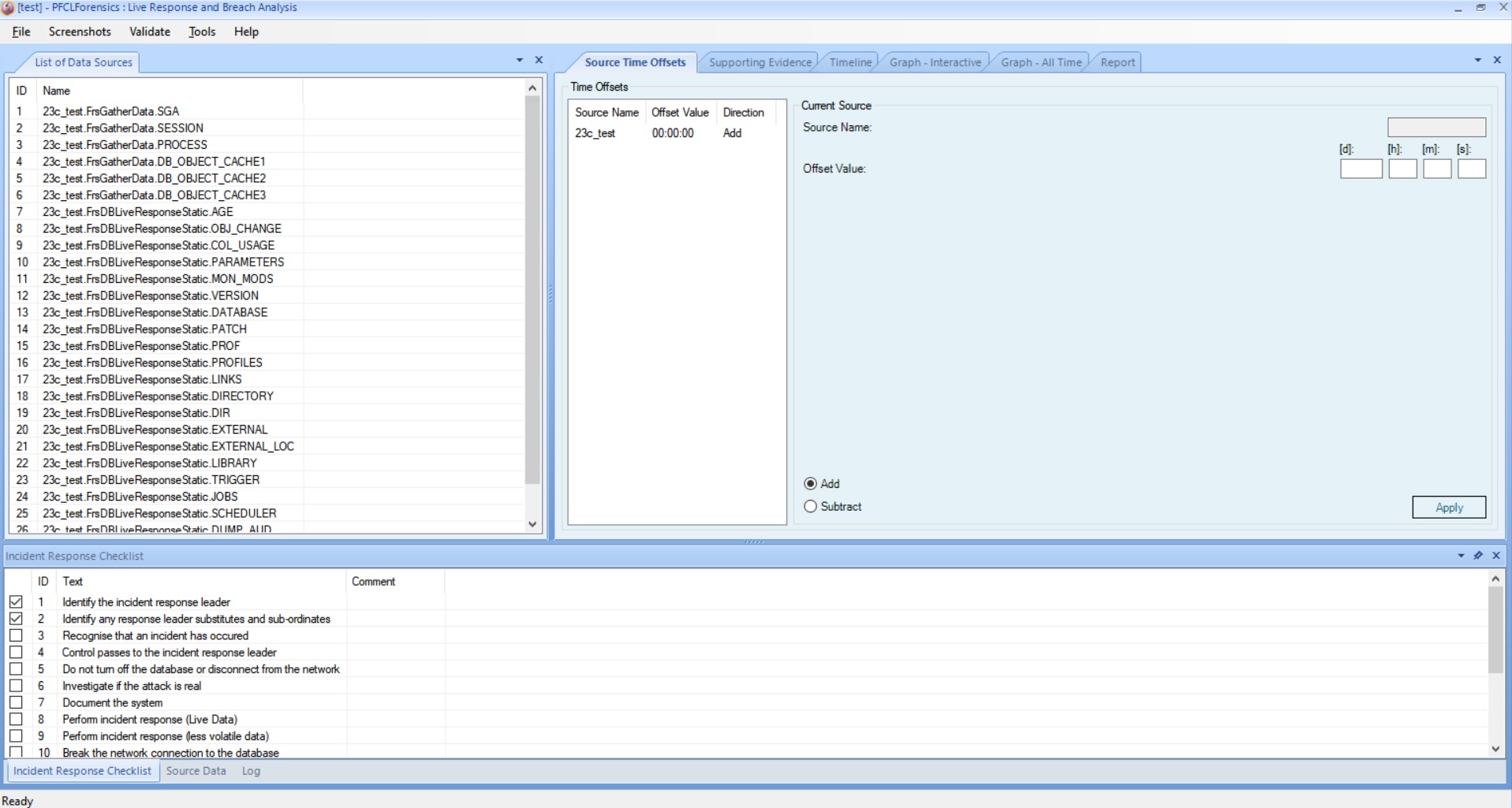
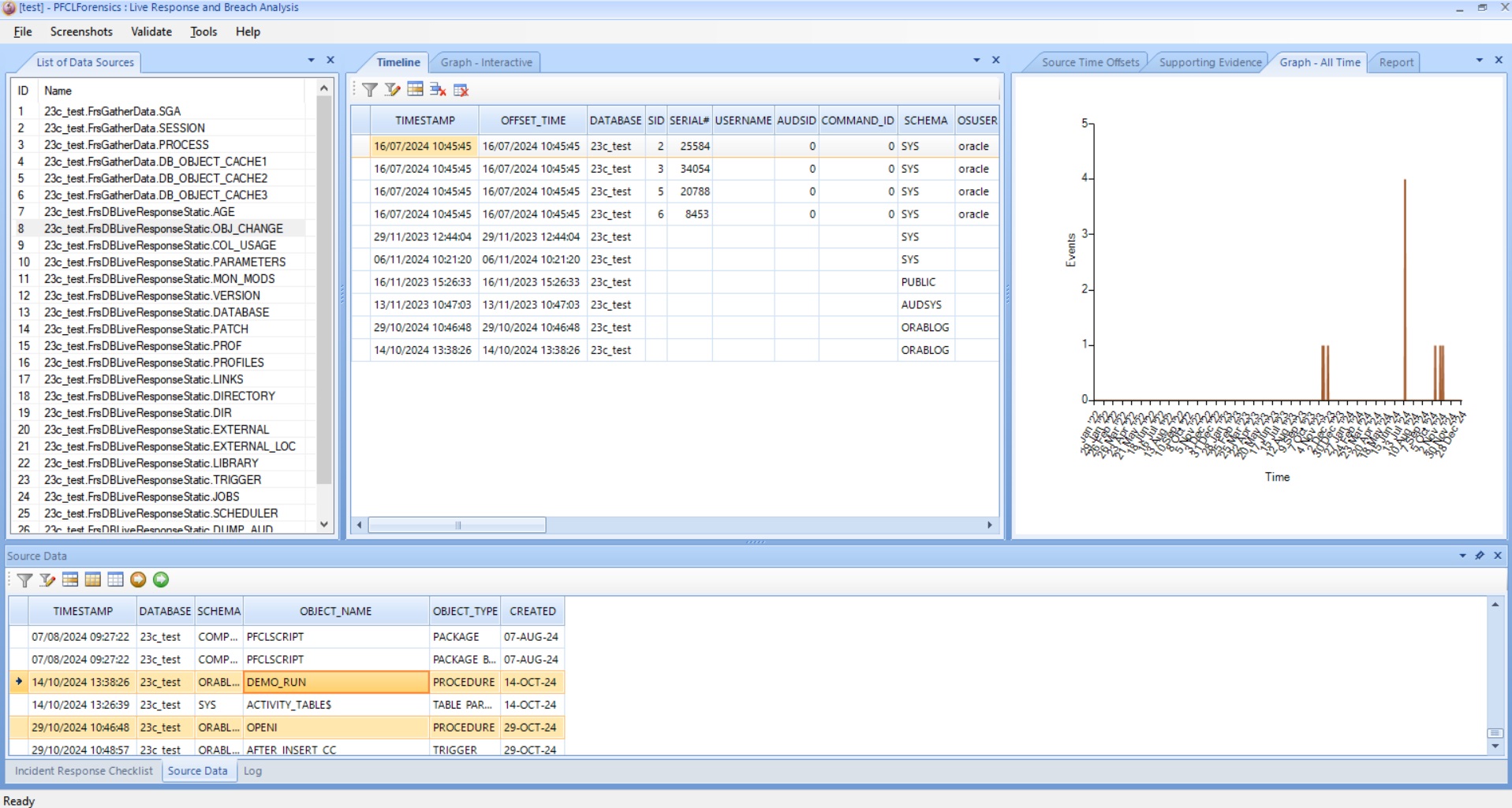
The above view shows the source data collected from the database for transient data (that data that changes easily and quickly) and static data (data that could change but is less likely to). As you can see in the view we can also adjust and align all time stamps so that all data when chosen to be part of the investigation is correlated with all other data. This could be because some data in the database is held as UTC or GMT and some with the local timezone; and further some data from a web server or PC may have further time differences maybe because the PC is not aligned with NTP. We can adjust all times as viewed and correlated with this feature.
The next step for the forensic analyst needs to do is review the raw data; this can be done clicking any row in the "List of Data Sources" and this raw data then shows in the "Source Data" grid at the bottom of the screen.
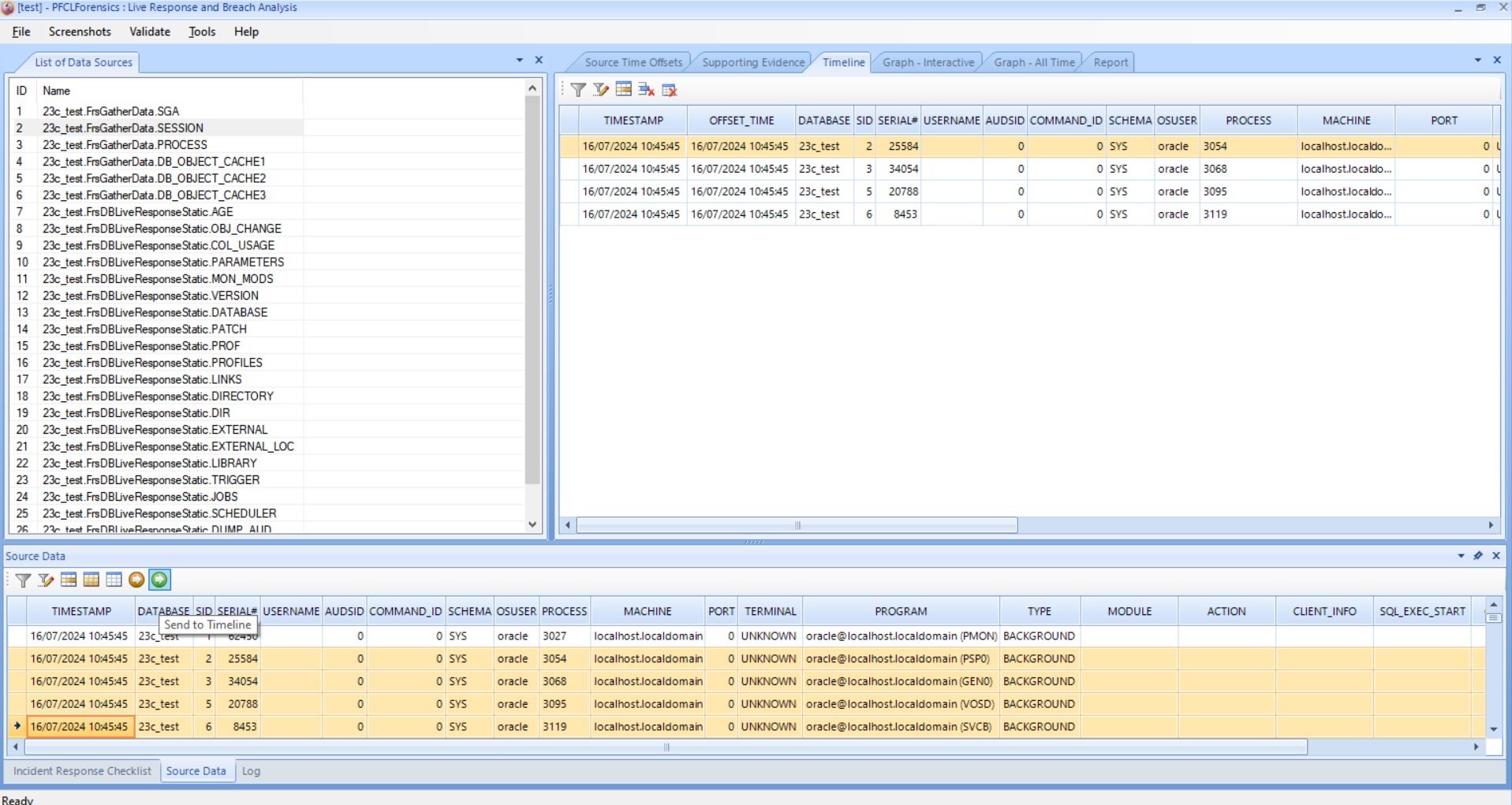
The view above shows the user selecting source data that maybe part of the attack and clicking the little green button to send this data to the timeline.
If data is deemed interesting but maybe not part of the actual breach then instead it can be sent to the supporting timeline. As we add data to the main timeline we can view drillable graphs of the events and also see all of the chosen data in a grid correlated across data points such as user name or timestamp so that all of the gathered data can be seen in the same time frame and also data context
Additional data can be added via the Import File menu option and added to the investigation. We include some standard data sources such as Apache access logs or Apache error logs BUT any data can be included. The user can simply create a new import type pattern by defining column types and then importing the data using the new type.
The analysis should now progress to the point where the attack start point and end point are known and the data gathered is between these two points. The validate button can be used at any point to re-validate that the input data used has not been tampered with. When enough evidence is available to answer the questions who, when, why, how then you can create a report. The product includes a built in word processor and a template that can be used or you can write your own report. All data in grids can be selected and copied directly to the report and there is a screen shot facility to allow screen shots of graphs for instance.
The goal is to understand in advance how you may manage and respond to a potential data breach or attack of an Oracle database under your protection. PFCLForensics allows this to be done more easily and to be managed.
It is really worth while understanding the process and tasks in advance of an actual breach. You do not want to be told to handle a breach and also learn how to do it in advance.
Practice in advance and also define and create your processes and teams
You might think, I don't care as it has not happened to me but you should care. It is really worth knowing in advance what to do and how to act and respond it a real breach or even a potential breach. Talk to us to see more of PFCLForensics and see a live demo arranged for you over webex or to purchase a license
#oracleace #sym_42 #oracle #forensics #liveresponse #databreach #security #forensicanalysis #forensics #hacking #datasecurity

















